Checking Open and Listening Ports on Linux Using netstat and ss
Monitoring open and listening ports on a Linux system is an essential practice for maintaining system security, performing network troubleshooting, and effectively managing your server infrastructure. 🛡️ By regularly checking which ports are open and which services are using them, you can stay ahead of potential security risks, identify unauthorized access attempts, and ensure that your system is not exposed to vulnerabilities. 🔍
Understanding which services are bound to specific ports helps in detecting misconfigurations or unexpected behavior, such as unfamiliar processes listening on sensitive ports. This knowledge can significantly reduce the chances of a security breach by providing the information needed to close unnecessary ports or secure the ones that are in use. 🚪🔒
In this article, we will cover how to use both netstat and ss commands to check open and listening ports on a Linux system.
1. Understanding Ports and Their Types
Before we dive into the tools, it’s important to understand the basic types of ports you may encounter:
- Open Ports: These are ports on which applications are actively listening for connections.
- Listening Ports: These are ports that a service or application has bound to and is actively awaiting incoming network traffic.
- Common Protocols:
- TCP: Transmission Control Protocol (reliable, connection-based).
- UDP: User Datagram Protocol (connectionless, less reliable, but faster).
2. Checking Ports with netstat
What is netstat?
netstat is a classic command-line tool that provides network statistics and information about network connections, including open and listening ports. Although it’s been deprecated in favor of newer tools like ss, it is still widely used.
Installing netstat
netstat is part of the net-tools package. On modern Linux distributions, you may need to install it manually:
- Debian/Ubuntu:
- CentOS/RHEL:
Using netstat to Check Open and Listening Ports
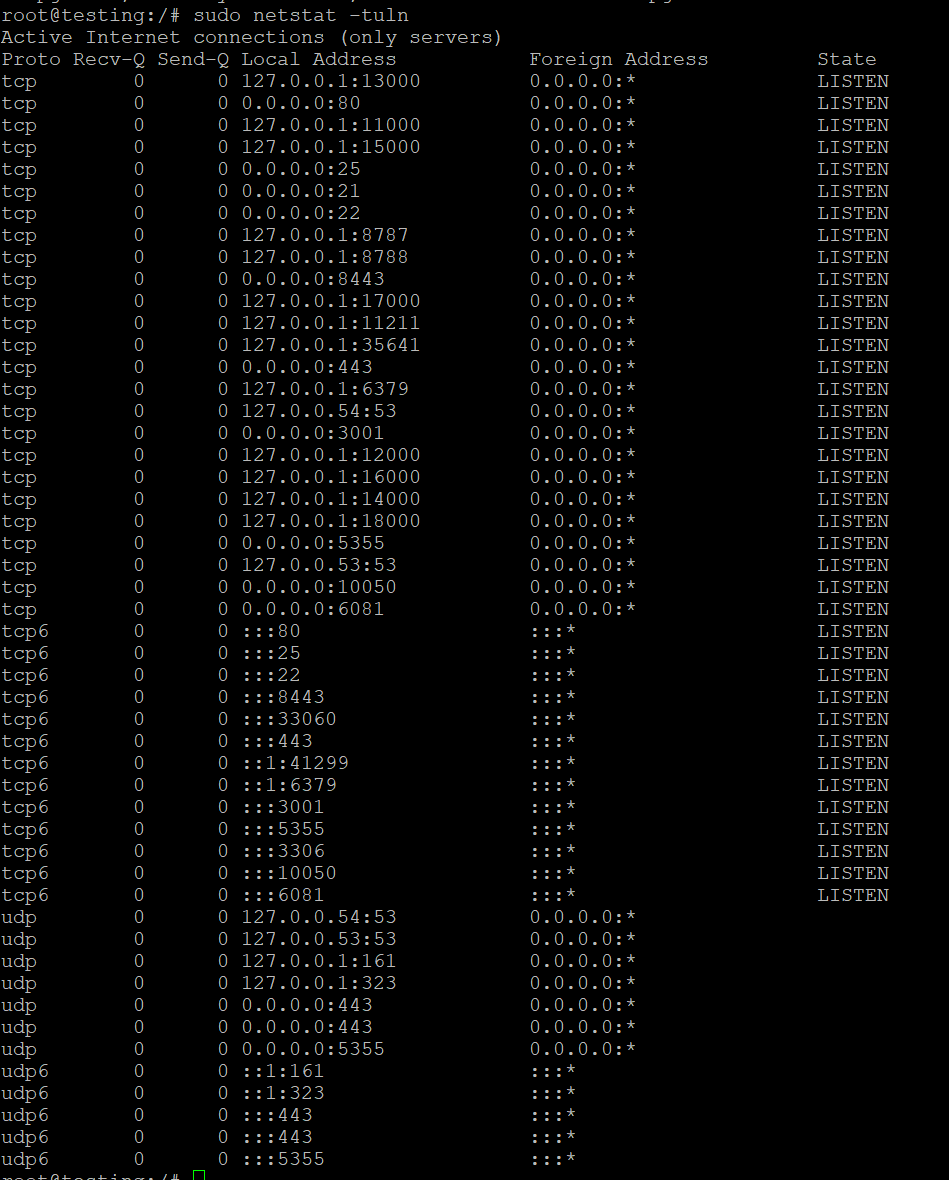
To check all listening ports on your system, including TCP and UDP, use the following command:
- -t: Show TCP ports.
- -u: Show UDP ports.
- -l: Show only listening ports.
- -n: Show numerical addresses instead of resolving hostnames and services.
Example Output:
- Local Address: The IP and port on which the service is listening.
- Foreign Address: The IP and port of the remote client (for active connections).
- State: The state of the connection (e.g., LISTEN for open ports).
Filtering Specific Ports or Services with netstat
You can filter the output to focus on specific ports or services. For example, to check for ports related to HTTP (port 80):
This will display all services listening on port 80.
3. Checking Ports with ss
What is ss?
ss is a modern utility that has replaced netstat on many Linux distributions. It is faster and more efficient than netstat, particularly when dealing with large numbers of connections. ss can display open ports, network socket information, and more.
Using ss to Check Open and Listening Ports
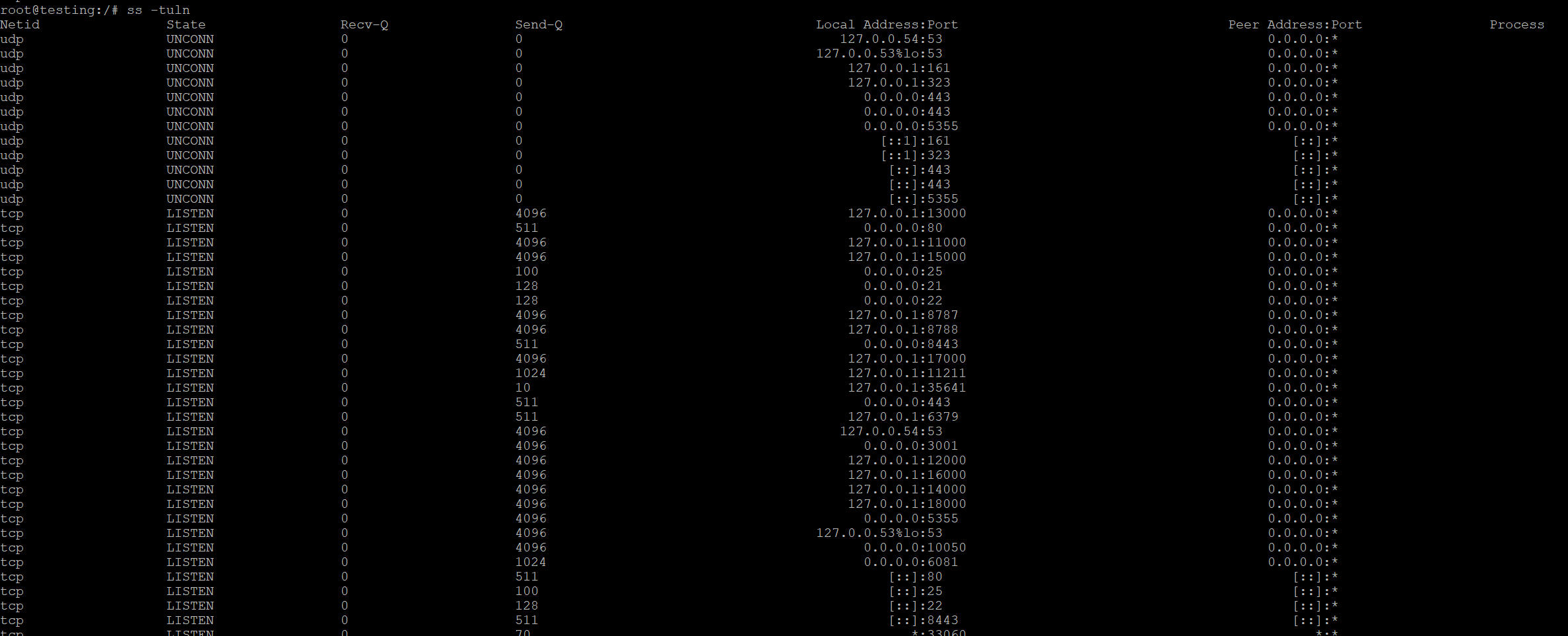
The syntax for ss is quite similar to netstat. To check all listening TCP and UDP ports, use:
- -t: Show TCP sockets.
- -u: Show UDP sockets.
- -l: Show only listening sockets.
- -n: Show numerical addresses (do not resolve hostnames).
Example Output:
This output shows all listening ports and their states (similar to netstat).
Advanced ss Usage
ss provides more advanced options to filter and display connections based on different criteria.
Display Listening TCP Ports Only:
Display Listening UDP Ports Only:
Display Listening Ports by Process ID (PID):
To see which process is associated with a listening port, use:
The p option shows the process using the port, which is helpful for troubleshooting.
4. Comparing netstat and ss
Both netstat and ss serve similar purposes, but there are differences worth noting:
- Speed and Efficiency: ss is faster than netstat and consumes fewer resources. It can handle large numbers of connections more efficiently.
- Availability: ss is included by default in most modern Linux distributions, while netstat requires installing the net-tools package on some systems.
- Output Format: Both provide detailed information about ports and connections, but ss has more options for filtering and displaying specific information.
When to Use netstat:
- When working on older Linux systems.
- When you’re familiar with netstat syntax and don’t want to switch.
When to Use ss:
- When you need better performance, especially on systems with a large number of connections.
- For more advanced filtering and network analysis.
5. Other Tools for Checking Open Ports
Aside from netstat and ss, there are other tools you can use to check open and listening ports in Linux:
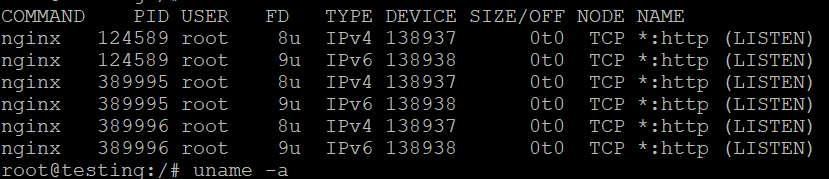
lsof lists open files, which can include network sockets. You can use it to check which process is listening on a specific port
This shows processes using port 80.
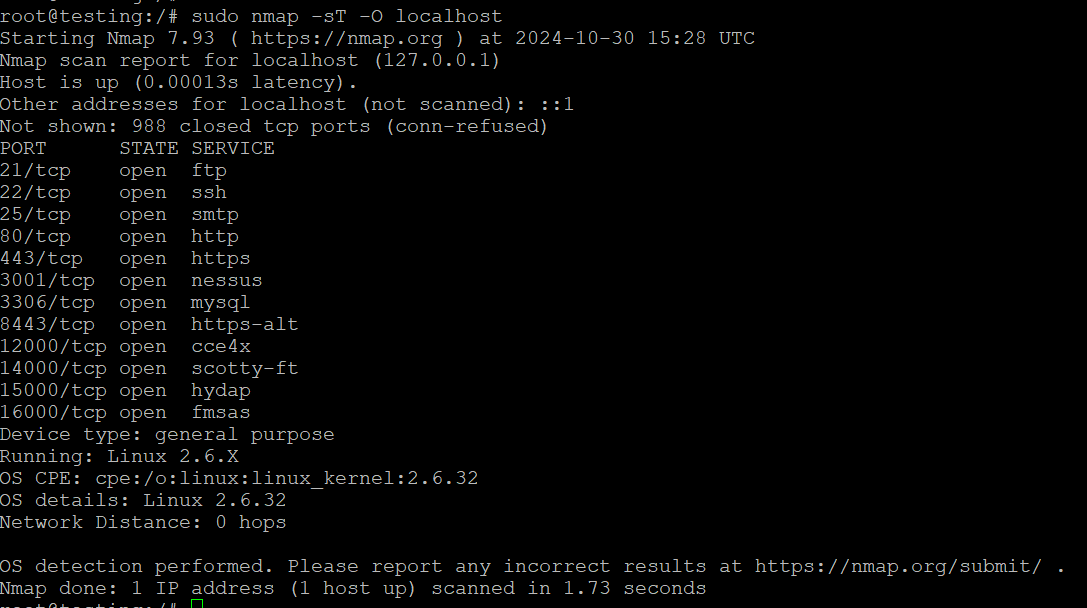
nmap is a network scanning tool that can be used to check for open ports on a system.
This command scans TCP ports on the localhost.
Conclusion
Monitoring open and listening ports is an essential task for system administrators, and tools like netstat and ss make this easy. While netstat is still used on older systems, ss has become the preferred tool due to its speed and efficiency. Whether you’re troubleshooting network issues or securing your Linux server, these tools will help you keep track of active services and ensure your ports are properly managed.
Use netstat if you’re more familiar with it, or switch to ss for faster and more efficient monitoring of your system’s open and listening ports.
Let me know if you need further clarification or help!